The past decade has seen an increase in predatory and fraudulent practices in digital finance and fintech. In the last 10 months, there has been an increase in anecdotal evidence that the COVID-19 pandemic has led to a proliferation in the methods and tools predatory and fraudulent providers are using to exploit vulnerable households and businesses (see recent media coverage here and here).
In exploratory work using high-frequency mobile application data for 71 countries, we document the increasing scale and scope of these new methods. We observe that some of the most downloaded mobile apps in a number of countries following the outbreak of COVID-19 include finance-related apps that show signs of being either predatory or entirely fraudulent. For example, there is a growth in personal lending apps luring new users to pay nominal service fees to obtain access to cheap loans, but which are revealed to offer no actual service. The release dates of these apps coincide with the onset of COVID and related government lockdowns and are initially buttressed by extremely high ratings driven by tens of thousands of apparently fake reviews. After a duration, some appear to be eventually removed or blocked on the app stores.
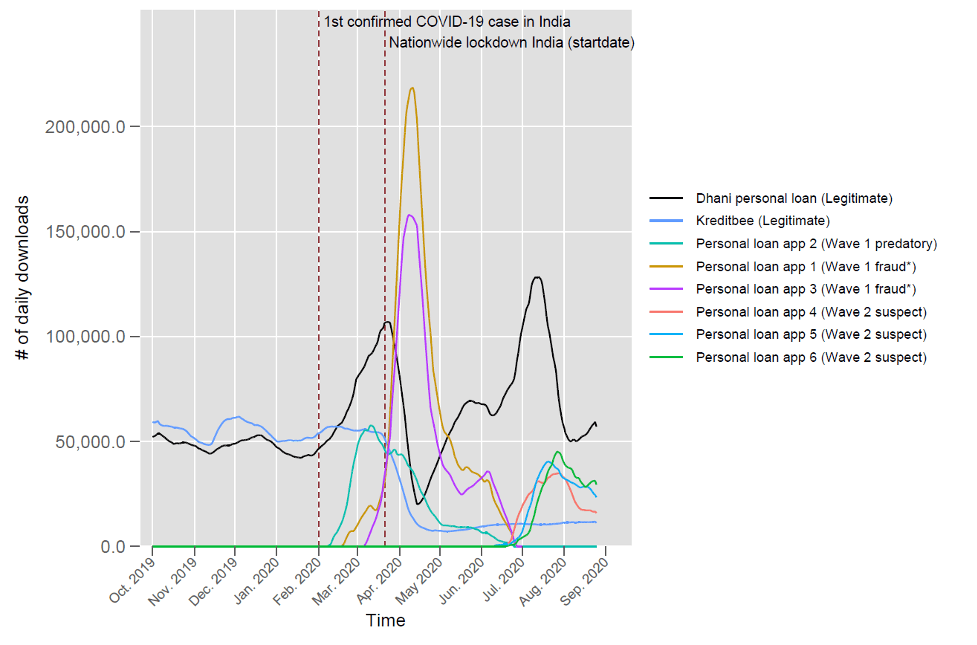
For this and other reasons, we categorize these apps as being highly likely instances of fraud. The graph below depicts this after the onset of lockdowns in India, where we saw a wave of lenders fitting these criteria pop up and quickly attract many users. Notably, the adoption of these fraudulent lending apps surpasses that of pre-existing lending apps from known, legitimate providers during this period. We also observe examples of apps set up to mirror legitimate sites (e.g., mimicking existing government or finance apps), but that appear to be designed to phish sensitive information from unsuspecting users. (India is used to illustrate such issues, but similar examples occur in a range of other markets, such as Nigeria, Philippines, etc.)
What are the Common Traits?
What seems particularly noteworthy about these cases are:
1. Ex-ante warning signs of the fraud apps
The apps and developers show a number of observable red flags, such as a lack of valid email address or provider website, and similarities across the suspect apps’ meta-data (e.g., icons, titles, descriptions), etc. This suggests that minor improvements to the vetting of these apps could significantly reduce the likelihood they make it to application stores.
2. Long Ex-Post Duration Before Shutdown
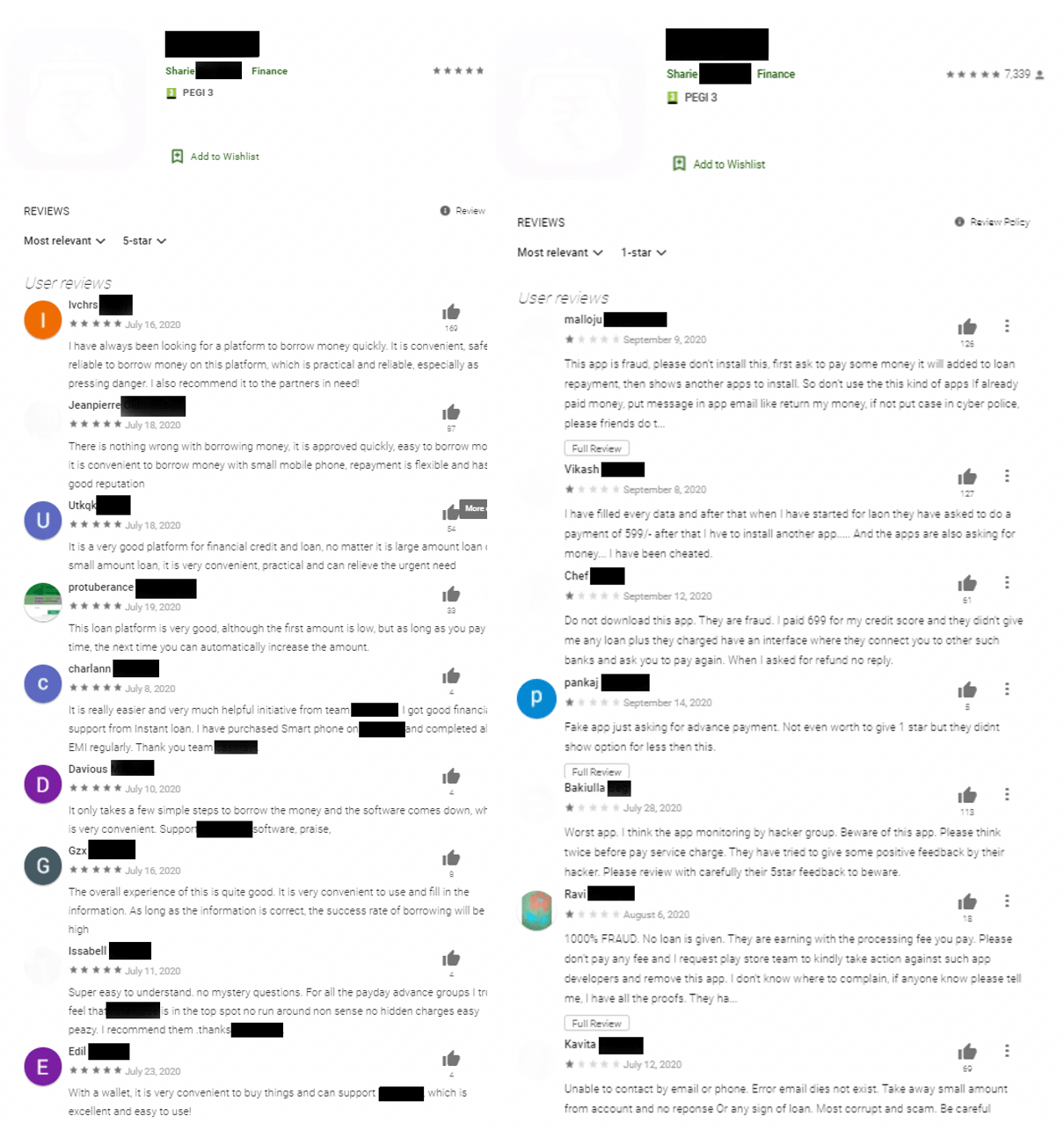
Many of these fraudulent apps remain available for several months after initial signs of complaints from users start to be raised. See, for example, the duration of “Wave 1” providers in the figure above. This usually follows a transition from the high ratings driven by suspected fake reviews. Examples of such fake user accounts and reviews are provided in the screenshots at the bottom of this post.
3. The Scale of the Problem
A current strategy used by app creators appears to be to release many similar fraudulent apps in a given market with the expectation that most will not get any uptake. The few apps that do catch on with users, however, are then often able to attract large numbers of victims.
4. The Cyclical Nature of the Problem
Once a fraud app is eventually caught and taken down, similar ones quickly pop up to take their place, with some changes to their descriptions and format. In the figure above, this is represented by the “Wave 2” providers, which exhibit many characteristics that are similar to “Wave 1” providers. This suggests that individuals or groups supplying the apps are organized and likely to keep evolving their methods and tools to stay ahead of detection.
What are the Solutions?
While the scale and scope of the identified issues is troubling, a silver lining is that they also help highlight suggested next steps that could be taken by a variety of stakeholders to mitigate issues on both the supply and demand sides. Such a response could include, but is not limited to, the following further research and interventions:
Identify Priority Markets and Catalog Country-Level Issues
A first high-level step would be to identify countries where issues of fraud or predation in digital finance appear most prevalent, and channel attention and funding to critically exposed areas. This stage could simultaneously be used to catalog in-depth patterns of fraud or predatory providers within priority countries. This could be organized by or tasked to global standard setting bodies, policy think tanks, or academia. The methods used to accomplish this could include:
- analyzing historical high-frequency app data disaggregated at the country level for signals of fraud
- desk research compiling prior cross-country demand-side surveys that have questions concerning fraud (and/or organizing ones as needed)
- compiling and analyzing past cross-country information from local regulators, including measures of complaints logged through consumer protection divisions.
Supply-Side Interventions: Historical and Real-Time
To improve outcomes moving forward, there will need to be changes to the ex-ante vetting and ex-post monitoring of finance apps in order to meaningfully curb the rise of such fraudulent or predatory fintech.
Ex-ante Vetting
Efforts should be made to work with global standard setting bodies, financial regulators, legitimate industry players (e.g., fintech associations), and the app stores to change some basic requirements for listing finance-related apps on their platforms. For example, providers of certain types of finance-related apps should have to provide—at a minimum – a valid email address, valid website, and legal information pertaining to their businesses. During times of lockdowns or other economic crises, it’s recommended that certain types of new apps — such as personal loan apps — be scrutinized more critically before approval, e.g., higher human touch verification for apps meeting at-risk criteria. (We acknowledge that a fine balance must be maintained as to not screen out legitimate providers whose products and services may provide a critical and timely lifeline for households and microenterprises.) Furthermore, as fraudulent apps are increasingly cataloged, new apps could also be prescreened to check for metadata that’s similar to that of known fraudulent apps during the vetting process (e.g., against a consolidated and periodically updated global database).
Ex-post Monitoring
Real-time high frequency data on mobile apps could be combined and used to create a system for reporting highly suspect apps in real-time to app stores or other pertinent stakeholders before they have time to gain traction with the wider public. While many app providers currently fall outside the typical purview of financial regulators, the adverse spillovers that predatory or fraudulent providers may have on legitimate and regulated providers may justify development of regtech or suptech tools for more broadly monitoring the app delivery platforms.
This could significantly reduce the lag between the release of problematic apps and them being taken down. Furthermore, since there are signs that many fraud apps in a given market are coming from the same suppliers or developers, it would arguably also be important to try and track down the most prolific of these and target them with legal action (e.g., block their payment, bring legal cases, enact fines, etc.).
Demand-Side Interventions: Financial Literacy and “Buyer Beware” Labeling
Digital financial literacy interventions could be undertaken in critical markets to disseminate information for consumers on simple signals they can use to identify and avoid fraudulent or predatory apps. For example, as economic crises unfold, governments and authorities can consider doing “just in time” campaigns about digital fraud. Legitimate industry players like digital lender associations can also play an important role by organizing, within their provider networks, communication to consumers. At the baseline, this could begin with flagging general patterns we have already observed in suspected fraudulent apps. As more information is collected, this could be supplemented with more localized information that better capture different techniques used.
Information gleaned from ex-post monitoring could be used to develop “buyer beware” labeling.
Alternatively, information gleaned from the ex-post monitoring previously described could be used to develop “buyer beware” labeling on the app storefronts to raise awareness for consumers on apps that have many signals similar to those known to be fraudulent. However, as the scams appear to evolve rapidly, any interventions or “buyer beware” labelling would need to be updated regularly.
Conclusion
While not all the above interventions may be possible, this discussion is intended to spark debate on the necessary coordinated response and concrete steps that must be taken to curb the rapid increase in fraud and predatory fintech during crises. The most effective solutions will likely include a multi-pronged approach: coordination between global standard setting bodies, local financial regulators, app stores, and other relevant stakeholders. It also highlights that the response must be envisioned with the long-term in mind (i.e., periodic checks and updates of methods to detect and mitigate) in order to keep up with the constantly evolving methods and tools used by such providers. Nevertheless, our exploratory work suggests that even some simple changes to vetting and monitoring may yield large improvements to mitigating obvious cases of fraud.